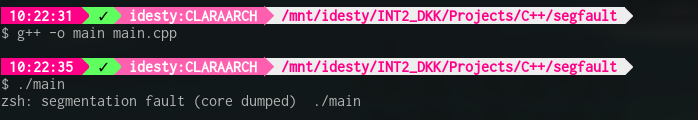
When you are programming in languages like C/C++, chances are that you get errors such as segmentation faults.
You know these errors well, probably. And you probably have come to hate them a lot.
However, as crazy as it sounds, you want segmentation faults when your program messes up. Yeah I said it, segmentation faults are your friends.
And I say that because they are errors that you can debug a lot more easily than ones that don't crash your program.
Now why do I mention all of this?
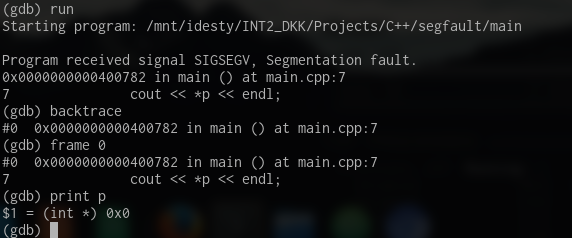
There are tools out there that can, when your program segfaults, tell you exactly where the issue is in your code. I'll introduce you to a fan-favourite, GDB.
GDB can, when used correctly, be used when your program segfaults to find out what variable, function, pointer, etc causes the crash.
|
Appearance
Language
About
|
SettingsSelect a category to the left.AppearanceThemeLight or dark? Choose how the site looks to you by clicking an image below.
LanguagePreferred LanguageAll content on utk.claranguyen.me is originally in UK English. However, if content exists in your preferred language, it will display as that instead. Feel free to choose that below. This will require a page refresh to take effect.About"utk.claranguyen.me" details
|